What Are WebRTC Leaks and How to Prevent Them?

Before we get to what WebRTC leaks are we need to know what WebRTC is. So what is WebTRC?
WebTRC is short for Web Real Time Communication. It is an open-source web protocol that now comes preinstalled in many web browsers and mobile applications. WebTRC allows these web browsers and mobile applications to share information among themselves in real-time. This information could be audio, video, or even text-based files.
WebRTC in itself was developed to create a standardized and efficient method to allow peer-to-peer communication in real time between web browsers and some compatible apps without the need for third party plugins or complex installations.
Many of today’s companies that offer video conferencing, voice calling, and live streaming services like Google, Zoom, Facebook, Snap inc, and UberConference, all use the WebRTC protocol.
How Does WebRTC Work?
Now that we know what WebRTC is, let’s quickly dive into how it works and mention some real life applications.
WebRTC uses a bunch of Javascript APIs and built-in browser components to function. The main APIs are:
-
getUserMedia: Used to access microphone and camera.
-
RTCPeerConnection: Used for setting up video and audio calls.
-
RTCDataChannel:Used for enabling peer-to-peer data transfer.
With these APIs, here’s a quick breakdown of how WebRTC operates:
1. Media capture
The very first step of WebRTC is media capture. In many cases, the media is the data that needs to be communicated between web browsers. To carry this out, when a WebRTC application is initiated, the API, getUserMedia requests access to your microphone and camera. The will usually appear as a pop-up tab on your browser with the options “allow” and “block”. Once you allow it, the media is then captured and ready to be displayed or transmitted.
2. Signaling
While signaling isn’t particularly standardized in WebRTC, it is still a crucial step of how it works. Before establishing connection, the connecting browsers or mobile applications must exchange information that will help them determine the best way to establish a connection. This information could be session control messages, network addresses or session media data. Signaling typically occurs via WebSocket, HTTP, or other similar protocols.
3. Create connection
The next API that WebRTC uses is RTCPeerConnection. With this API, connection parameters like the codec and other media settings are negotiated, and agreed upon. After this, WebRTC uses Interactive Connectivity Establishment (ICE) framework to determine the best path to connect with peers, and a direct peer-to-peer connection is established.
4. Data transfer
Once connection is established, the media data, which could be audio, video, or even text files can now be transmitted between peers in real time. The data is also encrypted using Secure Real-time Transport Protocol (SRTP) for media data and Datagram Transport Layer Security (DTLS) for non-media data. This ensures that the data is protected and secure during the transfer
5. Media communication
While the media data is being transferred, WebRTC components manage the bandwidths, media encoding, media decoding, noise reductions, echo cancellations, and network fluctuations.
6. Data channel communication
The last WebRTC API, RTCDataChannel, is what handles this part. This part covers the transfer of other data forms asides media. This data could be text chat, gaming data, or file transfers.
7. Session termination
When the communication is complete, the session is then terminated using the same signaling process that was used to establish it.
Now that we know how WebRTC works, let’s list some of the real life applications:
-
Google’s gaming platform, Stadia.
-
Internet of Things.
-
File transfer in Torrents.
-
Financial applications and trading platforms.
-
Augmented and Virtual Reality.
-
Voice and video calls.
-
Customer support and live chats.
-
Online education and e-learning .
What are WebRTC Leaks?

Knowing that WebRTC connections require the exchange and transfers of confidential information during the signaling and create connection phase, we can infer what happens during a WebRTC leak.
So what are WebRTC leaks? WebRTC leaks are security breaches that occur during a WebRTC transfer that could lead to your IP address being exposed.
Your IP address is a crucial part of your online anonymity, and if compromised, could expose your location and your ISP(Internet service provider). This information, in the hands of malicious hackers could lead to a lot of problems for you.
WebRTC leaks are definitely dangerous when they occur, and if you use browsers like Firefox, Opera, Chrome, Microsoft Edge, and Opera, you’re at a bigger risk of having these leaks. Mainly because these web browsers come with WebRTC enabled by default.
How to Check for WebRTC Leaks
Here are some ways of checking for WebRTC leaks:
1. Online WebRTC leak tests
Right now, there are multiple online WebRTC leaks tests that you can use to check if you have any leaks on your browser some of the more popular ones include:
2. Manual WebRTC leak tests
If you don’t exactly trust online WebRTC leak tests you could manually check. The process is quite tedious but here’s a quick breakdown of how to carry out a manual WebRTC leak test on Chrome.
-
Open a new Chrome Window in incognito mode
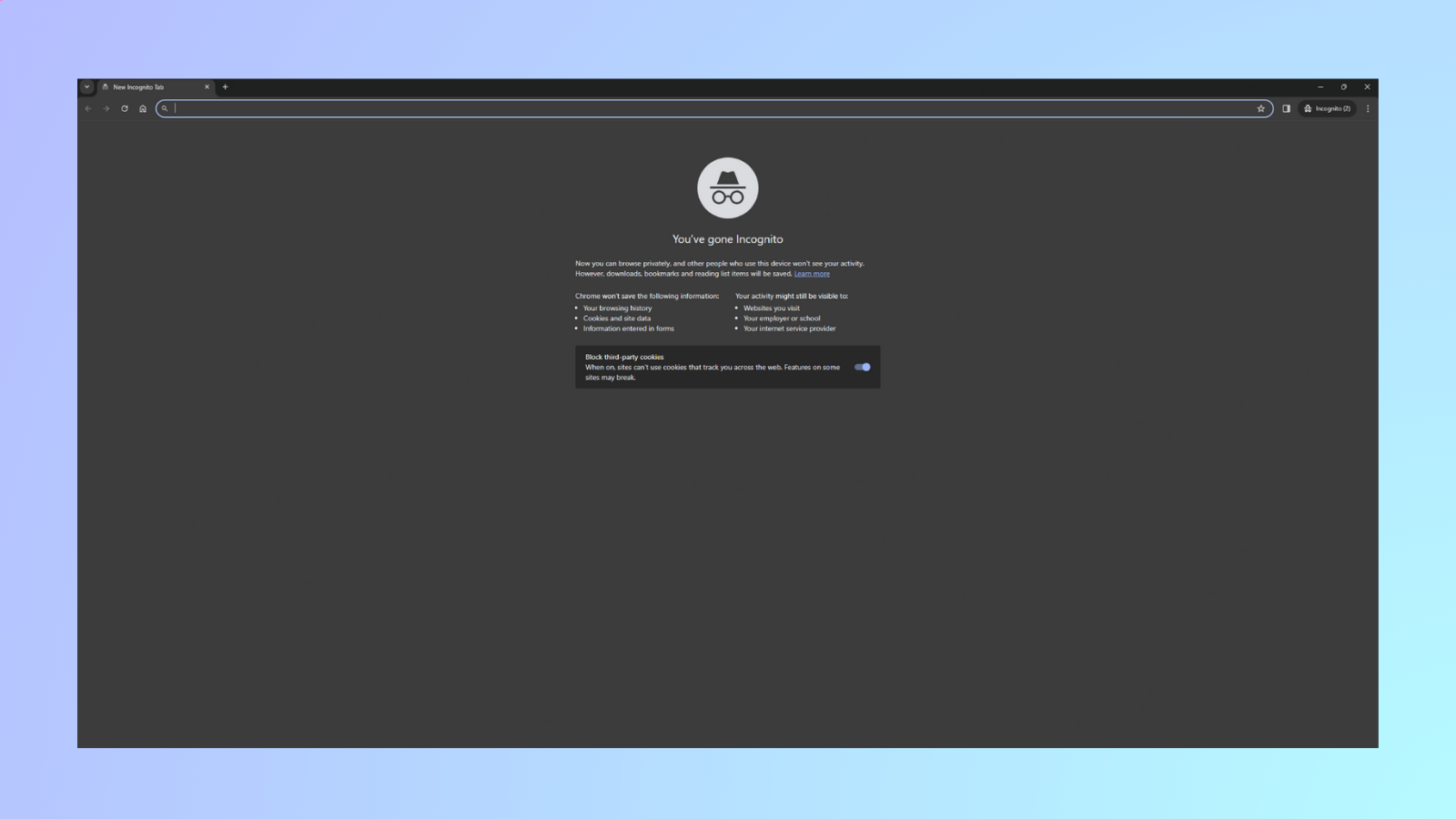
-
Right click on the window and select “inspect page”. This should open Developer tools
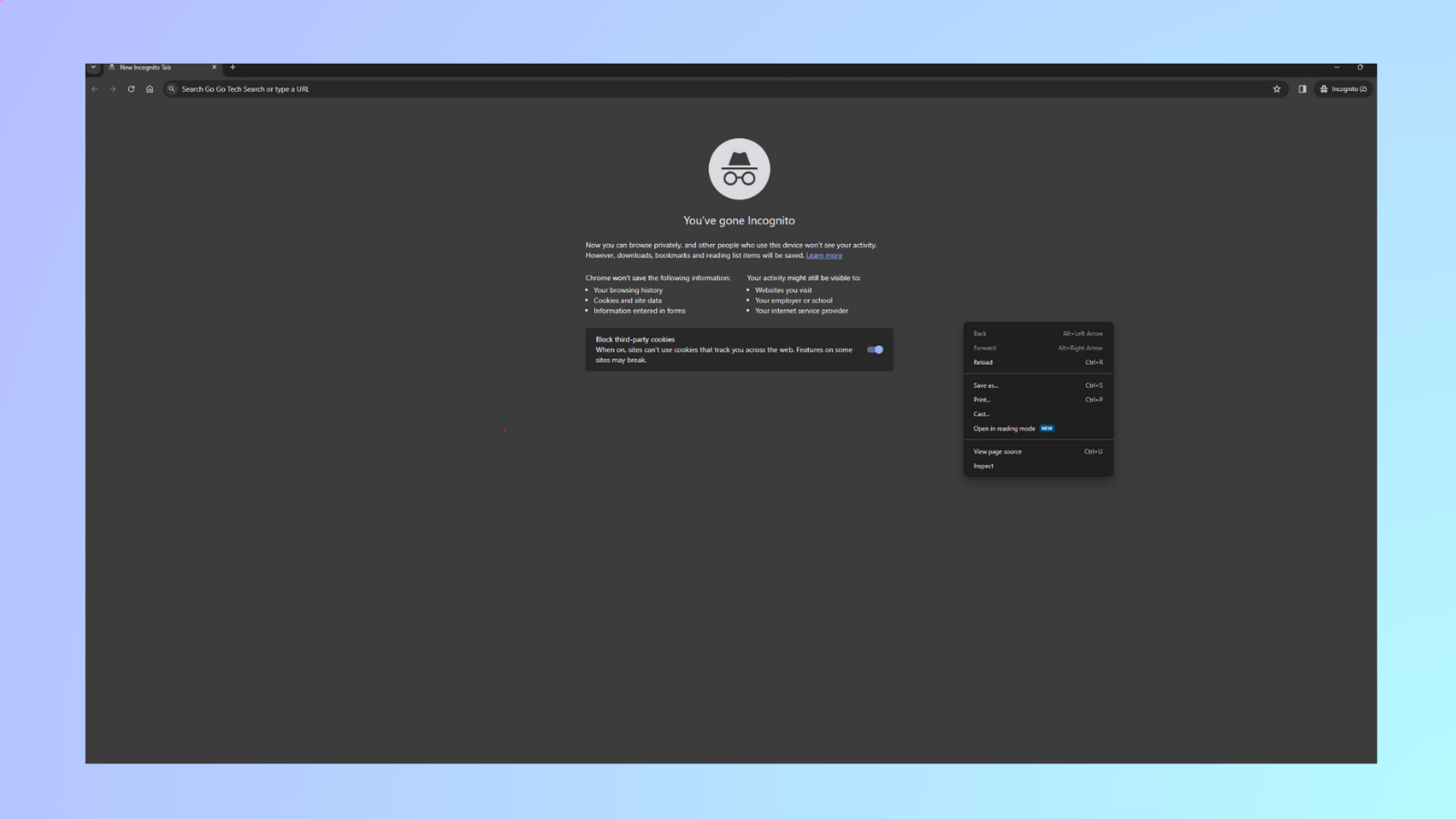
-
When this comes up, go to the “Console” tab.
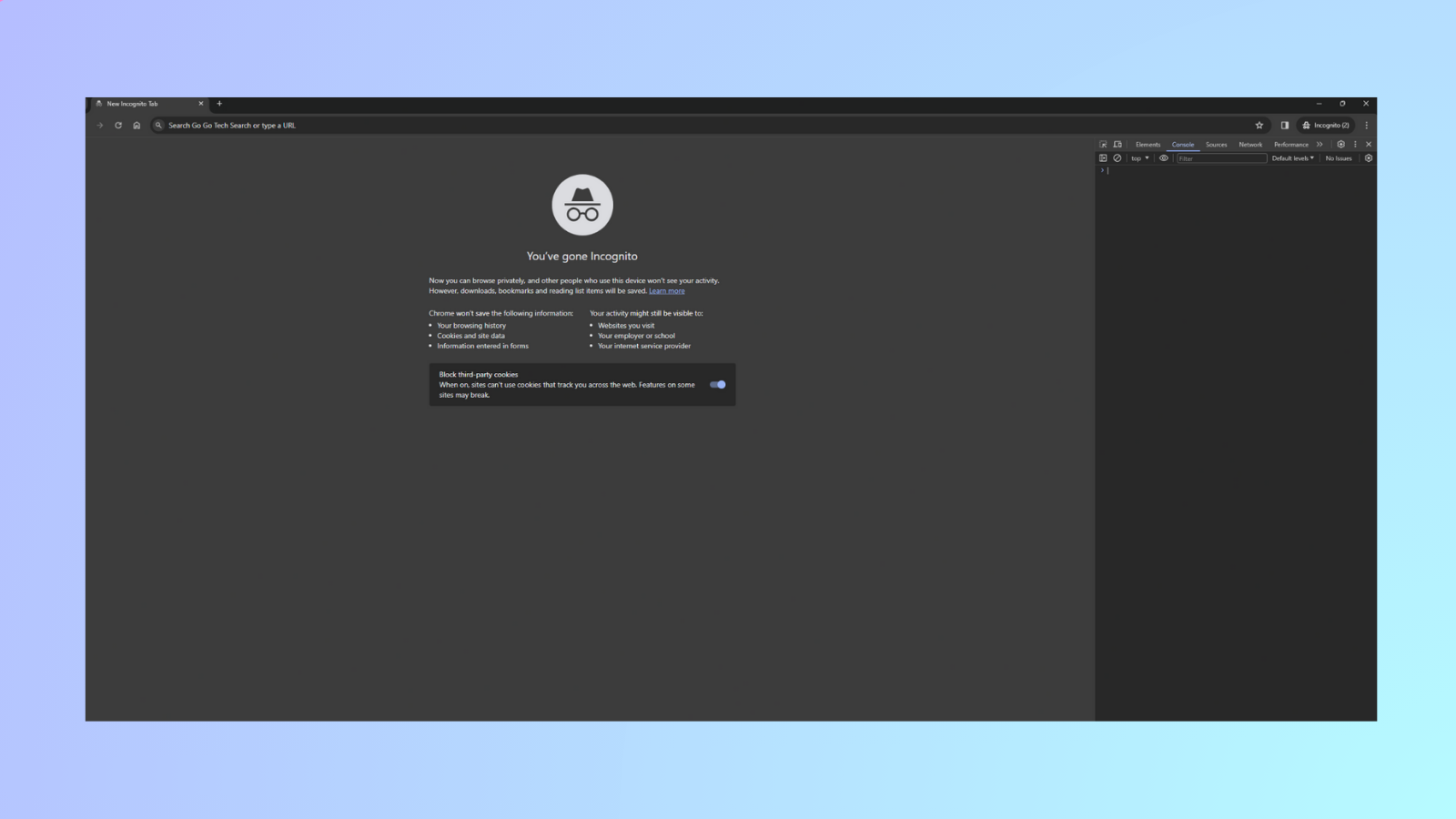
-
Copy and paste this code:
var rtc = window.RTCPeerConnection || window.mozRTCPeerConnection || window.webkitRTCPeerConnection;
var pc = new rtc({ iceServers: [] });
pc.createDataChannel("");
pc.createOffer(pc.setLocalDescription.bind(pc), function() {});
pc.onicecandidate = function(ice) {
console.log("IP Address: " + ice.candidate.candidate.split(" ")[4]);
};
-
Type “allow pasting” and run the code.
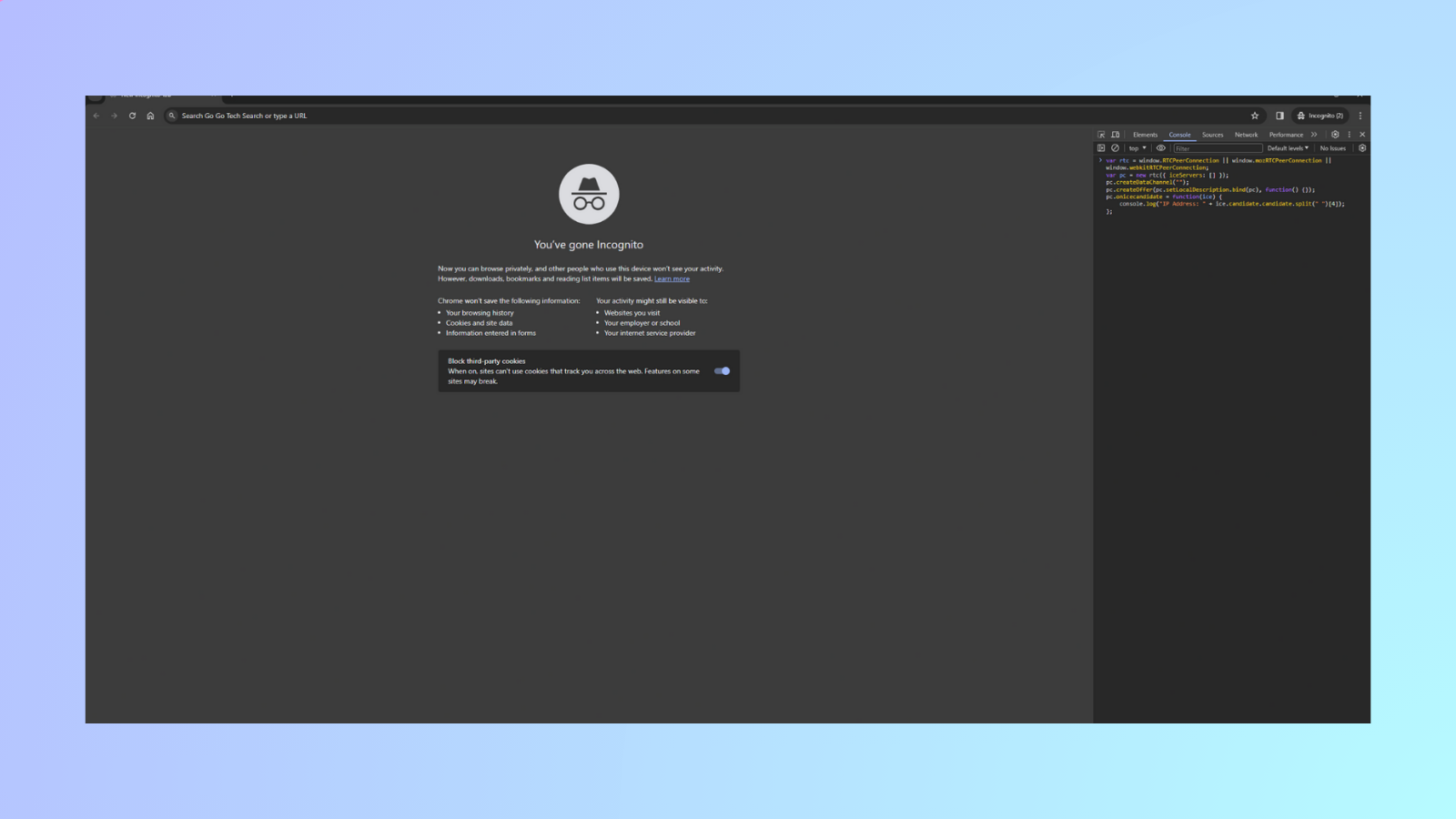
After running the code, if the IP address that comes up is your actual IP address, you are at risk of experiencing a WebRTC leak. (You could check your IP address here.)
This process is just for Google Chrome on Windows and Mac. Other browsers are much more difficult to check, but we will touch on how to prevent WebRTC leaks on these other browsers in the “How to block WebRTC leaks” section of this article.
3. Use WebRTC leak test browser extensions
The final method of checking for WebRTC leaks is by simply adding browser extensions to your browser and running them. Some of the more reputables ones include WebRTC Control (Chrome, Firefox) and uBlock Origin.
How to Prevent WebRTC Leaks
Let’s get into how you prevent WebRTC Leaks:
1. Disable WebRTC on your browser
Let’s take a look at how to disable WebRTC on the desktop versions of these browsers.
How to disable WebRTC on Firefox browser
-
Type about:config into the address bar
-
Click the “I accept the risk!” button
-
Type media.peerconnection.enabled in the search bar
-
Double-click to change the value to “false”
How to disable WebRTC on Opera browser
-
Go to settings on your Opera browser
-
Expand the Advanced section on the left-hand side and click Privacy & security
-
Scroll down to WebRTC and select the Disable non-proxied UDP radio button
-
Close the tab and the settings should automatically save
How to disable WebRTC on Microsoft Edge browser
There’s no way to 100% disable WebRTC on your Edge browser, but you could mask your IP during WebRTC connections like this:
-
Type about:flags into the address bar
-
Check the option marked “Hide my local IP address over WebRTC connections”
2. Use browser extensions
The browser extensions method of preventing WebRTC leaks works for Chrome and Firefox browsers. And just like with WebRTC leak tests, the most reputable extensions for preventing WebRTC leaks are WebRTC Control (Chrome, Firefox) and uBlock Origin. There’s also WebRTC Network Limiter for Chrome.
3. Use a Proxy or VPN
A great VPN could do a great job of masking your IP address. So even if a WebRTC leak occurs, the IP address that’s leaked, turns out to be a fake one. Some great VPNs like ExpressVPN also allow you to forcefully disable WebRTC in your browsers using their extensions for Chrome, Firefox, and Edge. Other VPN you can try include SurfShark VPN, and NordVPN.
4. Use an antidetect browser
The last and perhaps the best way of protecting yourself from WebRTC leaks is by using a very good antidetect browser. A good antidetect browser does more than mask your IP address; they also spoof your digital fingerprints. Making you 100% anonymous while you are browsing.
Options of preventing WebRTC leaks in AdsPower
Open the AdsPower app and navigate to the browser profile settings page. Here, you'll find WebRTC in the Advanced section. We'll guide you through the four methods to prevent WebRTC leaks in AdsPower:
-
Forward: Forward via Google to mask real IP. Used for high-security websites(Ebay and Discord).

-
Replace: WebRTC enabled. Public will be replaced by proxy IP and Local IP will be masked.
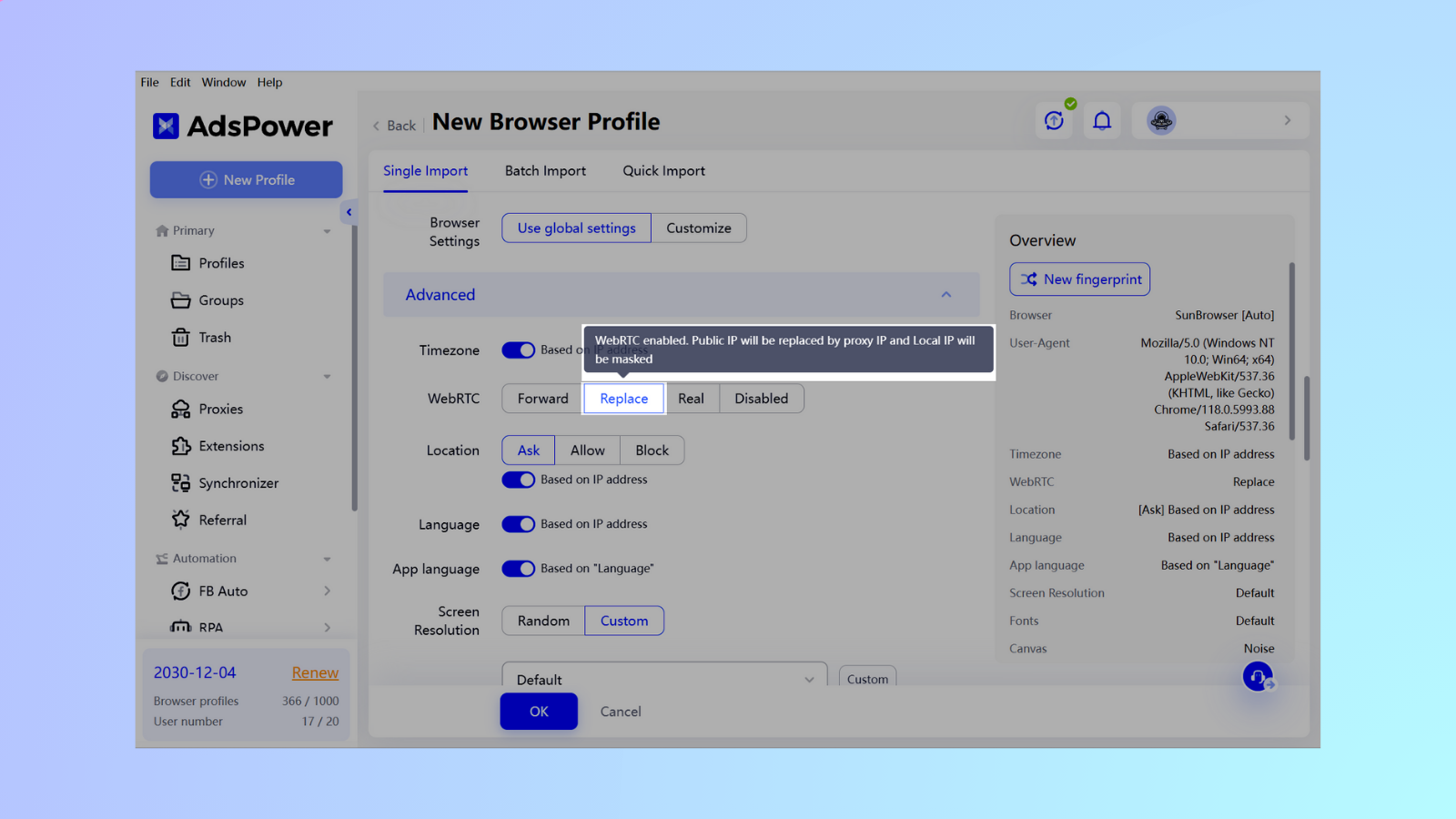
-
Real: WebRTC enabled. Your real IP address will be used.
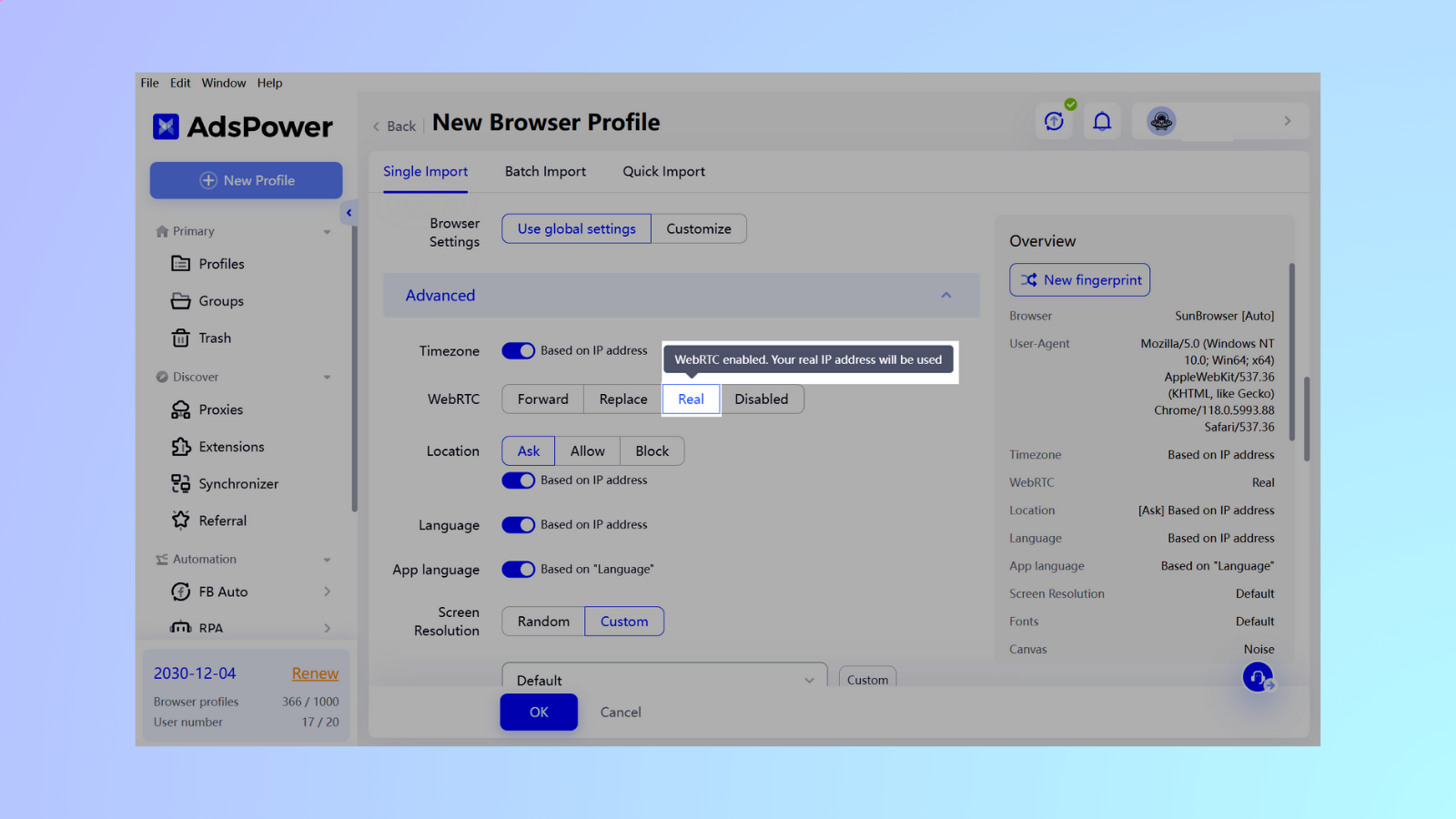
-
Disable: WebRTC closed. Website will detect that you close the WebRTC.
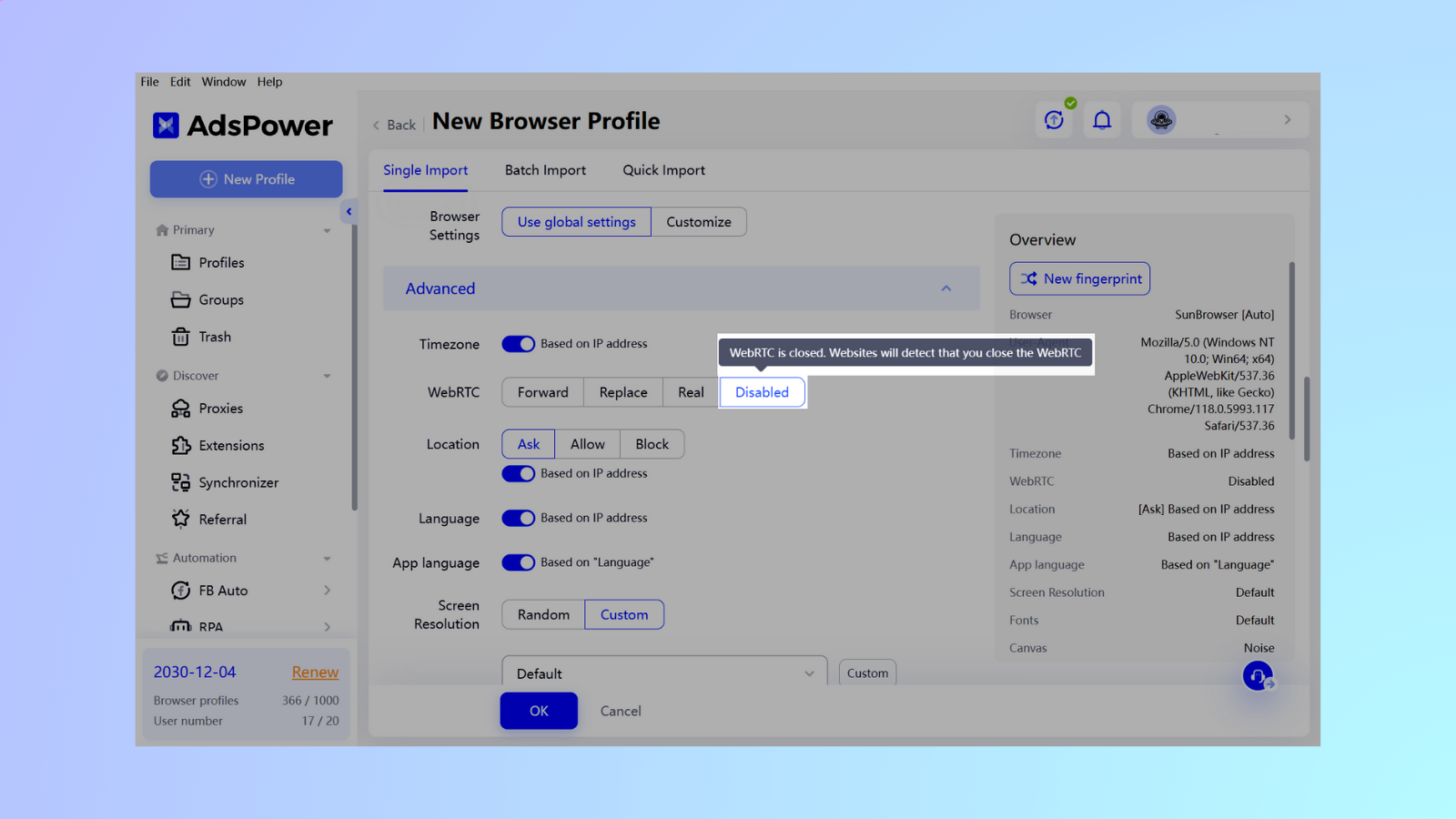
WebRTC masking can offer stricter privacy requirements in some cases by bypassing proxy servers for certain data, like media. However, this forwarding mode requires transmitting data through a transit server, which can potentially slow down communication. Speed impact increases with stricter masking: Disable > Forward > Replace > Real.
Finding the balance: The level of masking you choose depends on your priorities. If anonymity is paramount, stricter settings might be worth the occasional inconvenience. But if seamless website access is crucial, a lighter touch might be better.
Conclusion
By now, you should know how useful WebRTC are, and how the pesky WebRTC leaks could end up exposing your IP address to the wrong people. You should also be aware of how you can carry out WebRTC leak tests to know if you’re at risk of WebRTC leaks, and also know how to prevent them.
All said, while there are many individual methods on this list to prevent WebRTC leaks, it would be best to go for a combination of two or more of the prevention methods just to be more certain. And if that feels like a hassle, just switch to using an antidetect browser, especially AdsPower, and you can rest assured that your online anonymity will remain uncompromised.

다른 사람이 읽은 항목
- Cross Browser Fingerprinting: User Tracking On Steroids
- Browser Fingerprinting vs Cookies: What’s The Difference?
- What is Font Fingerprinting_ A Detailed Guide!
- What are HTTP Headers: Understanding Key Players of Client-Server Communication
- Breaking Down What Is A User Agent: UA Components & How To Look It Up


