What is Browser Fingerprinting?

Browser fingerprinting is the third avenue of user tracking after cookies and supercookies. Fingerprinting is initiated by websites that analyze the requests sent by HTTP clients to uniquely identify a specific machine by collecting a digital fingerprint. Data acquired in this manner can be used to continually track users even after cookie deletion.
In our brief article, we will outline the basics of browser fingerprinting, how it’s used to track internet users and what can be done to reduce the likelihood of being recognized through the details sent.
How does browser fingerprinting work?
Browser fingerprinting is an active way of data collection which hashes unique browser parameters and creates a digital signature. Websites can add additional JavaScript code (either by creating their own script or buying from third party providers) to an HTTP request response. The JavaScript code scans all public browser parameters and creates a unique digital signature from the data.
Data acquired through employing additional JavaScript code includes user agents, screen size and resolution, installed fonts, plugins and extensions, GPU/CPU, etc. Each data point adds to the uniqueness of the device, allowing websites to identify a particular machine more easily.
Browser fingerprinting is becoming increasingly ubiquitous. Numerous websites, including top ranked websites, are utilizing fingerprinting to identify new and returning users. Search engines like Google and Bing are no exception and have been employing various measures to identify specific users.
Advanced browser fingerprinting versions can provide even more data on the machine, mostly through accessing HTML5 Canvas and requesting some measure of graphics processing. Employing HTML5 Canvas can reveal the operating system, browser, and GPU of a machine. HTML5 Canvas generally requests the browser to render a specific image. Due to slight differences in how GPUs render images, device-specific details might be acquired.
Finally, extreme measures include analyzing clock skew. Clock skew is when the electrical signals from one source (mostly from the clock generator) arrive at different components unevenly. These differences are affected by hardware temperature variations. Thus, with enough data and numerical analysis, clock skew differences can be measured to determine hardware specifications and many other aspects of a machine.
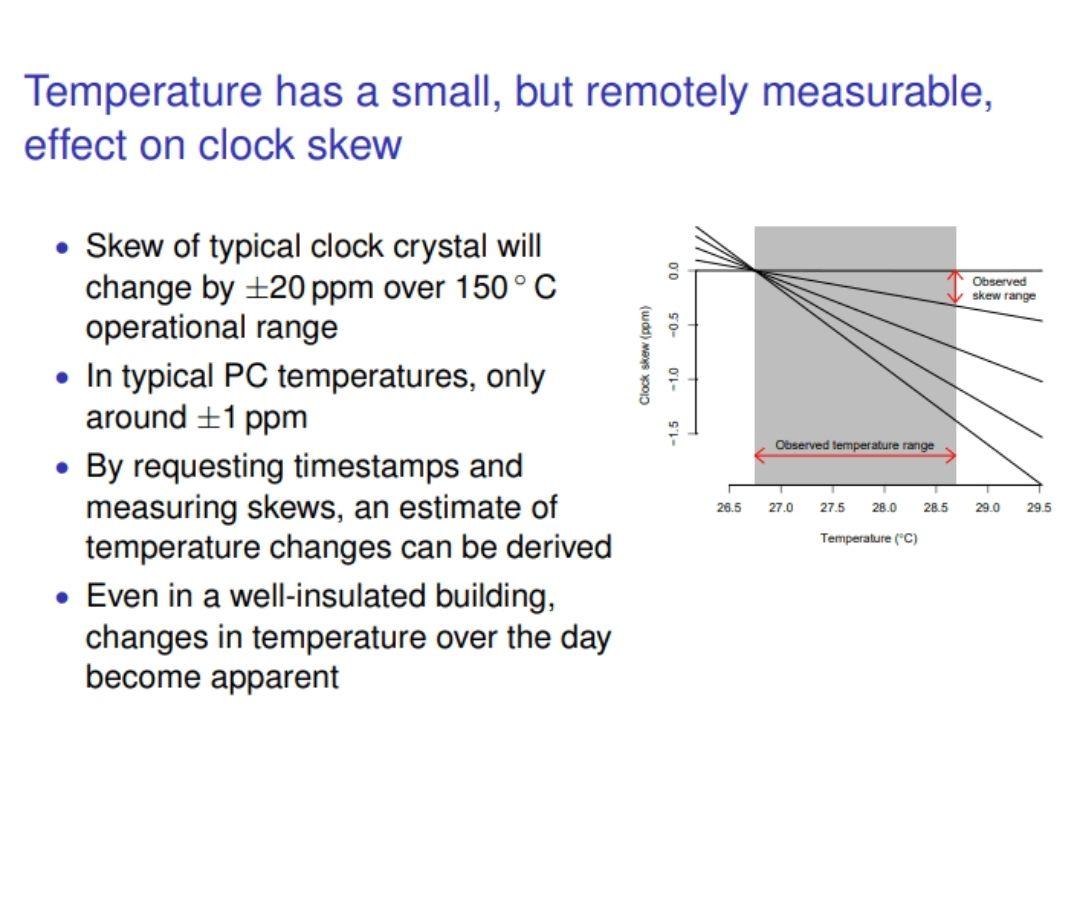
Temperature changes might be used to gather data on devices utilized by a machine.
Source: Hot or Not: Fingerprinting hosts through clock skew
Understanding browser uniqueness
Browser uniqueness is the determining factor in whether a user can be recognized. To put it simply, browser uniqueness compares one device to many other computer fingerprints to find possible duplicates. If very few copies exist in the data set, the device is considered to be unique.
As a large amount of data about a particular device and browser can be collected, a user might be identified by the website as unique even without having access to cookie data. A study by The Electronic Frontier Foundation (EFF) found that only 1 in 286 777 browsers will share its fingerprint. Such a high level of browser uniqueness means that the same user can be easily recognized purely through fingerprinting.
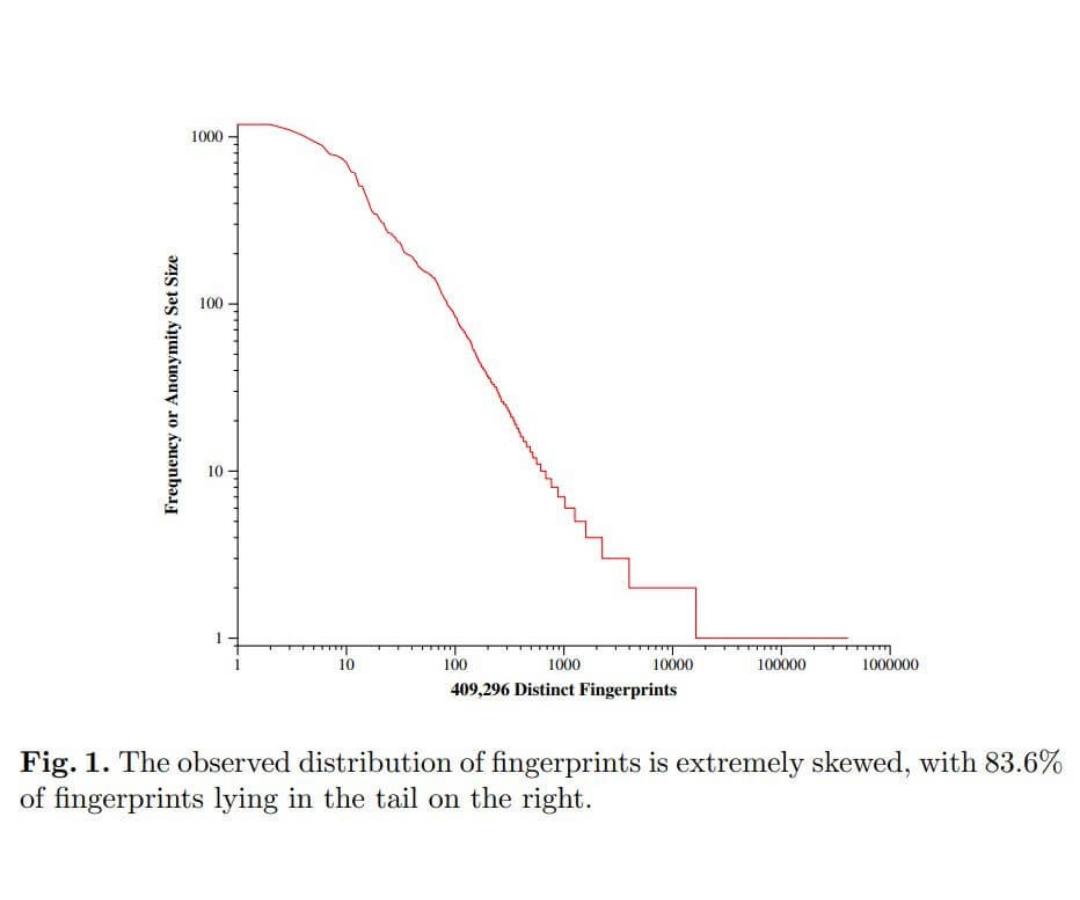
Source: How Unique Is Your Browser?
Note that the global uniqueness of fingerprints might be even worse as the study participants were likely to be more tech-savvy and privacy-conscious than the average internet user. However, accurately predicting the global uniqueness of a fingerprint seems to be nearly impossible. A mathematical limitation is apparent due to the difference between an experimental sample and the global set of fingerprints.
The existence of unique fingerprints may seem puzzling at first glance. To the average internet user, most browsers might seem rather similar. However, uniqueness is often determined by the amount of information divulged by plugins. For example, JavaScript version data often includes numbering that is only intended for debugging purposes (e.g., 1.6.0_17). As there are numerous minor changes over the development process, a single plugin might have hundreds of different versions. Combining the details of the browser, all its plugins, and many other data points can create millions of uniquely identifiable devices.
Improving browser uniqueness
Browser uniqueness can be tested by using a project developed by EFF: Panopticlick. The Panopticlick browser fingerprinting test will reveal all data collected about your device, and provide possible options to defend against it.
If getting tracked by large companies isn’t your cup of tea, then lowering browser uniqueness is the most effective option for fingerprint protection:
-
Use a commonly used browser. Running odd browsers (e.g., Comodo IceDragon) will greatly increase the likelihood of having a unique fingerprint.
-
Avoid custom user agents. Unique user agents are a surefire way to stand out from the crowd.
-
Reduce the amount of plugins used. Uniqueness is severely impacted by the amount of plugins installed in a browser.
-
Narrow down the preferred language list. Requesting pages for different languages greatly increases browser fingerprintability. For example, TorButton requests only EN versions of websites by default.
-
Use TorButton. TorButton implements most of the security features used in Tor Browser to a Firefox browser.
-
Disable JavaScript. Disabling JavaScript is an extreme measure that will break almost all websites. Yet, EFF finds that NoScript (an extension that allows users to switch off JavaScript) users were the most resistant to fingerprinting.
Ironically, anti-fingerprinting solutions and plugins that are supposed to enhance privacy and reduce uniqueness can often have the opposite effect. Installed plugins (and their versions) can be detected, which means that they often add to rather than subtract from browser uniqueness.
We recommend experimenting with these options, utilizing the Panopticlick test, and browsing around the internet to find the most suitable combination. Using all the options listed above at once will likely break a lot of websites without providing clarity on what exactly happened.
Conclusion
Browser fingerprinting is becoming more common as a tracking measure. Unlike previous generations of tracking tools (e.g., HTTP cookies), defending against browser fingerprinting is significantly more difficult. Improving browser uniqueness is one option, yet the most effective measure is disabling JavaScript, which might cause client-side issues when displaying websites.
In this context, a good way to beat browser fingerprinting is to use the browser management tool. In our next post, we’ll introduce AdsPower, an affordable and effective browser management tool, and show how it can help in here.

Mọi người cũng đọc

